The cybersecurity landscape is constantly changing – that is why we have brought you some data to look at, so that you can more effectively protect your company network from the attackers. This time we will look more closely at phishing, an increasingly popular technique of tricking people to give up data, download malware, or otherwise compromise their company’s security.
The user is the weakest link of the cybersecurity perimeter – and the hackers know it
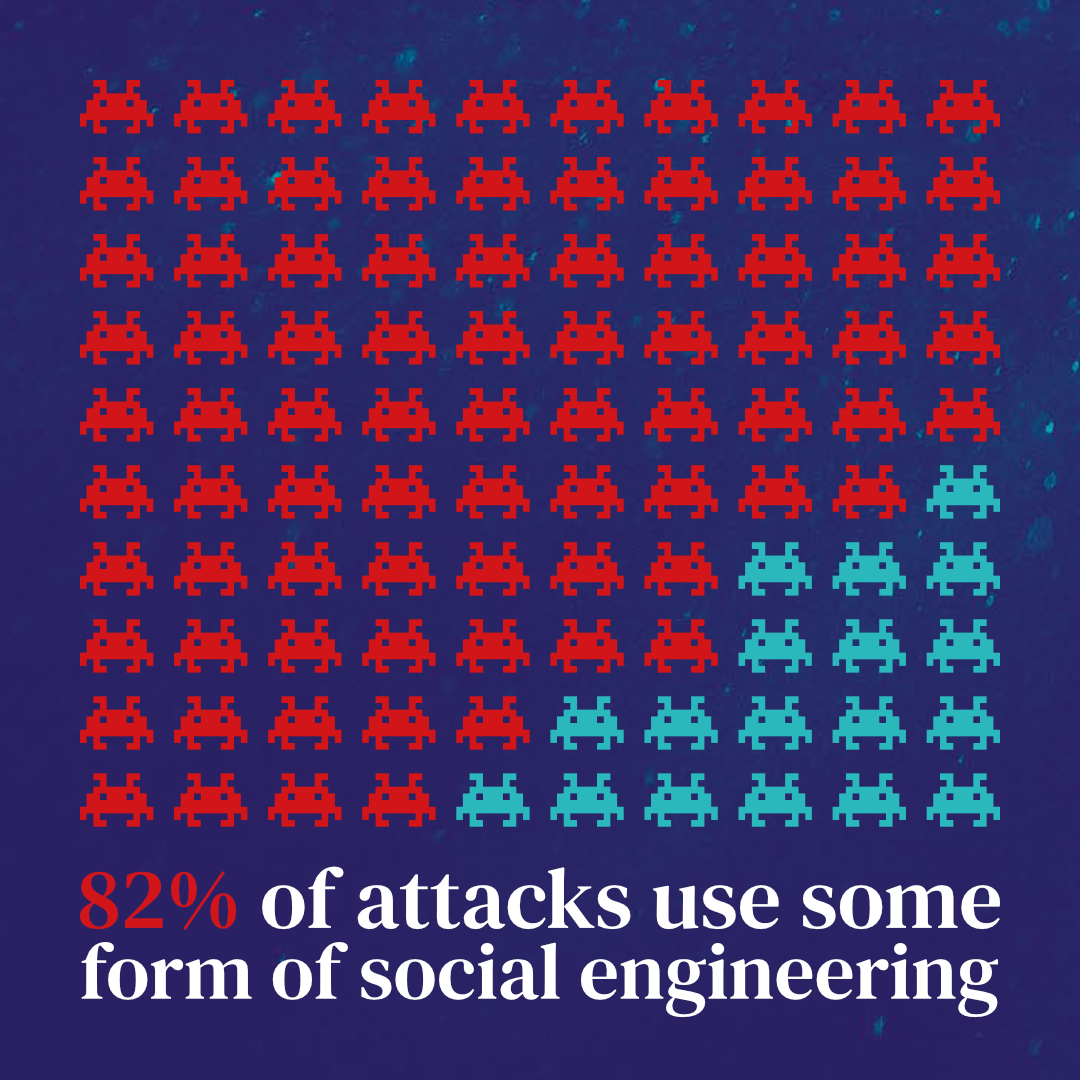
According to Verizon's 2022 DBIR, 82% of data breaches involve a human element, including phishing and the use of stolen credentials. This emphasizes the importance of organizations implementing strong authentication measures, such as multi-factor authentication, to prevent unauthorized access to sensitive data.
DNS protection has the advantage of looking at the domain itself, not only the activity in the device or the traffic. Moreover, Immunity analyzes the domains based on huge amounts of data from various external sources, own research, and data from our telco, ISP, and corporate customers – this way, Immunity detects even the brand new threats which are not yet in any threat intelligence database.
Impersonating the authority is still the favorite way to phish
KnowBe4 reports the top phishing email subjects globally, including emails posing as Google Docs, HR policy updates, and IT reports. This highlights the importance of user education and awareness in identifying and avoiding phishing attacks. In 8 out of the top 10 subject lines, the attackers impersonate someone with authority over the employee or their accounts.

Nevertheless, the e-mails change constantly and with the new AI possibilities, distinguishing the genuine e-mail from the fake one will be increasingly difficult. That is why, apart from prevention and proper staff trainings, it is vital to employ a solution which prevents human mistakes, such as Whalebone Immunity.
Data are power, and apparently they are easily stolen, sold and bought
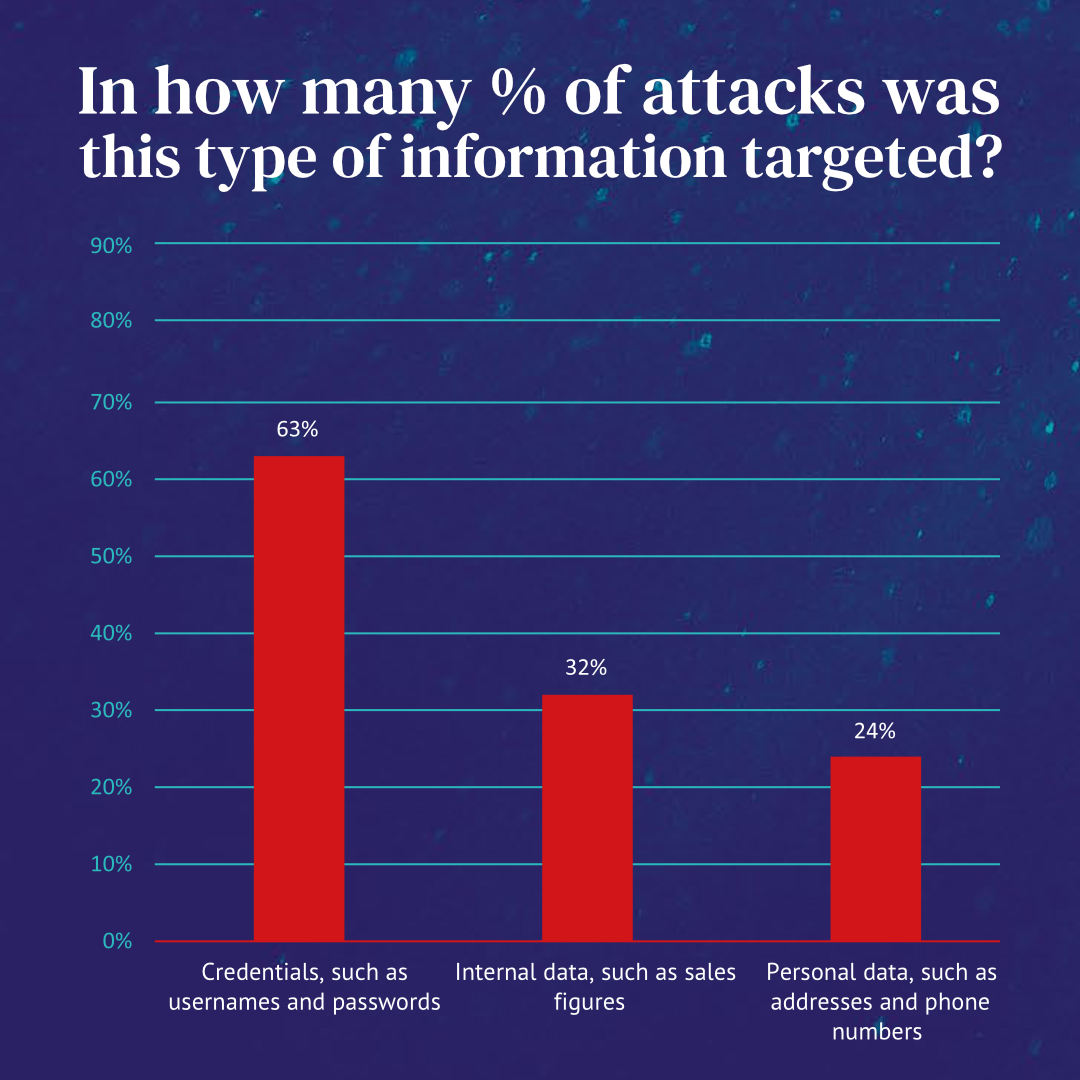
According to Verizon, credentials (such as usernames and passwords) are the most commonly compromised data in social engineering attacks, followed by internal data (such as sales figures) and personal data (such as addresses and phone numbers). This highlights the need for organizations to implement strong security measures to protect against social engineering attacks, such as advanced threat detection and response solutions like Whalebone Immunity.
The hackers can not only utilize the breached data, but they often sell them on the dark web. Basically anyone can for a few dollars buy a list of breached data and try to log-in into company e-mails, internal databases, and more. That’s why Immunity recently incorporated Identity protection into its feature-list – Immunity lists all of the identified breaches connected to customer’s domain in the past 10 years and alerts them of any new ones.
Working from home is a huge benefit – for both the employees and the hackers
A 2021 research by IRONSCALES found that 84% of IT professionals agree that working from home has made the employees more susceptible to phishing attacks. This highlights the importance of organizations implementing measures to protect against phishing attacks not only in their own network, but anywhere their employees work, be it on work trips, in cafés or at home office.

Whalebone Immunity’s Home Office protection is an effective way to widen your cybersecurity perimeter even beyond your company network. Make sure your employees are protected on DNS level anywhere they go.
Do not let your network be compromised.
Apart from prevention, there are some ways to mitigate the risks – such as Whalebone Immunity, which radically expands your cybersecurity perimeter and as one of the results, it will block your employees from accessing malicious domains. But that is just a tip of the iceberg – contact our expert Adam Wright and request a free trial to eliminate the blind spots in your security architecture.



