Amazon's Route 53 was subject to a massive Distributed Denial of Service (DDoS)
On October 24, 2019, Amazon informed its customers that Route53 was subject to a Distributed Denial of Service (DDoS) attack and that there was a disruption in the name resolution process. In more detail, the attack affected mainly the naming system of the S3 buckets.
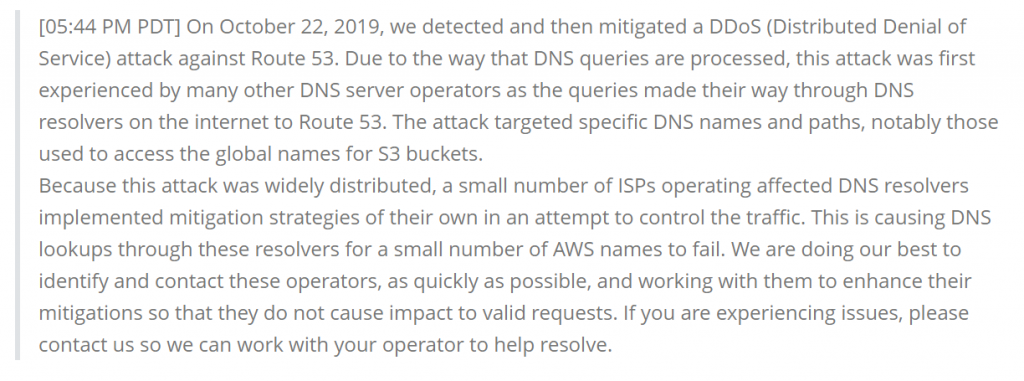
This situation could fall into the category of Slow Drip attacks. In this kind of attacks, a malicious actor continuously sends queries to the authoritative nameservers of the domain that they are targeting. The queries contain mainly non-existing pseudo-random subdomains. A direct result of this flood of queries is that the resources of the victim’s nameservers are depleted and eventually they stop answering even to legitimate requests.
Some indicative queries that were found in the traffic of the recent attack confirm this pattern:
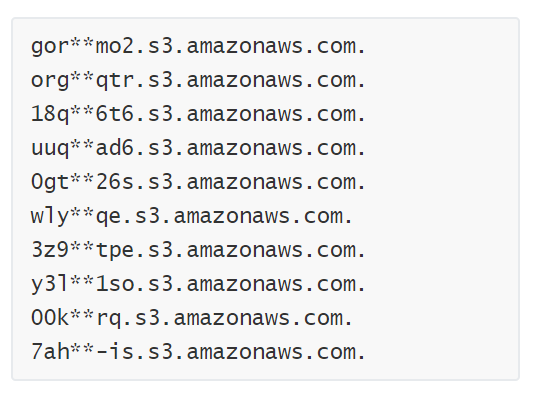
Whalebone identified the attack
In the case of Amazon, Whalebone was successful in timely identifying this attack and informing their affected customers.
Some early indication of the upcoming events can be traced back on October 19 when there was a spike in the DNS requests on Amazon’s domains. This could be considered as a testing cycle before the final outbreak.
Get protected with DNSSEC
A possible defence against this kind of attacks could be the introduction of aggressive usage of DNSSEC-validated cached answers. According to this specification, NSEC/NSEC3 resource records could be used to cryptographically prove the inexistence of a domain (or subdomain in this case).
By taking advantage of this, the compatible resolvers that are performing DNSSEC validation can deduce an answer to a query directly by their cache and thus drastically decrease the number of requests to the authoritative servers.
Whalebone’s security-enhanced resolvers are based on Knot resolver’s technology that, since version 2.0.0, supports this approach and guarantees resilience when facing this kind of attacks.
DNSSEC has to be configured properly
Unfortunately, Amazon’s DNS zones are not cryptographically signed (as can be seen below), and thus the cache-based inexistence proof could not be applied during the recent attack.
It is worth mentioning that even though Whalebone’s resolvers could not protect Amazon’s servers, they were not affected by the Increased malicious workload and the customers’ quality of service remained consistent.



