Coronavirus is rapidly spreading across the world and leaving a trail of disrupted businesses, daily lives and national and global economies in its wake. In an oddly prophetic move, in February 2020, Netflix released a new series aptly titled “Pandemic – How to Prevent an Outbreak” in which copious health experts, pointing to the 1917 Spanish flu pandemic that claimed millions of lives, claimed that another pandemic was not a question of “if”, but “when”. Unfortunately for us as a species, that when is now. Governments and health care professionals across the globe are issuing guidelines and emergency measures in an attempt to stop the deadly spread of the virus. With social distancing a compelling tactic to this end, hundreds of millions of people are being asked to isolate themselves, stay at home and, for non-essential services, work from home. Schools are closed and families around the world are wondering how to pass the time. Turning to the internet for information, work and entertainment is now, more so than ever before, an essential part of everyday life.Yet, as we have all seen in the early stages of the Coronavirus pandemic, with exposure comes risk. When it comes to the internet, with more people online than ever, more users are exposed, and malicious attackers are finding new ways to exploit the vulnerable and our concerns.
Key word based attacks
As we search the internet for more information about what is going on to assuage our own fears, cyber criminals are ready, willing, and able to exploit our compelling need to know. Due to the pandemic, as Andronikos Kyriakou, a technical consultant at Whalebone points out, “only in the last two weeks, we have seen a 7% daily increase in the number of unique domains that our users communicate with. There are indicators that 4% of these domains are linked with some kind of malicious behavior.” Whalebone statistics show that coronavirus- related domains are 50% more likely to be malicious than other domains registered at the same period.
Fake news and information
According to a recent report by Zack Doffman at Forbes, even Coronavirus maps are being used to plant malware to extract passwords, personal information and credit card details from unsuspecting victims. “Users do not need to download apps to run risks, malicious websites can also infect computers. And so you should avoid accessing any unknown coronavirus sites or clicking random links under any circumstances. This particular .exe file pretends to come from Johns Hopkins, and mimics the university’s real map,” writes Doffman.
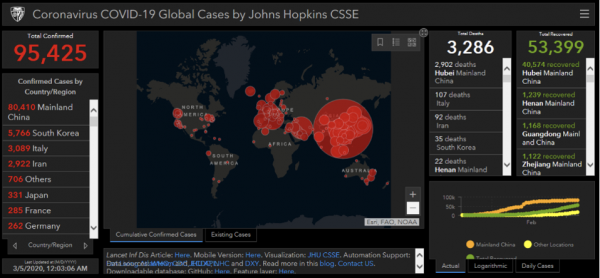
Coronavirus malware map. Source: forbes.com
Ransomware attacks
Closer to home the threats get even more real. Security Week wrote that “On March 13, 2020, it was reported that the Czech Republic's second-largest hospital, the University Hospital Brno, which has a major COVID-19 research laboratory, was hit by ransomware.” The attack shut down the entire network of the clinic, imperiling the lives of both patients and health care workers and stopping mission critical work. The site went on to report that “Researchers from Cybereason Nocturnus have been tracking the rise and variety of such attacks, which now include phishing, fake apps and ransomware. Phishing has followed the spread of COVID-19 infections, fake apps are targeting the growing number of home workers, and ransomware is targeting healthcare organizations.”
Phishing attacks
Even the World Health Organization (WHO) has issued a press release warning internet users to beware of cyber criminals pretending to be the WHO and specifically referencing Coronavirus. Known as phishing, these types of attacks use email to elicit users to provide sensitive information, click on malicious links or open malicious attachments, under the guise of being a reputable source of information.The fake page not only shows a page that looks like the WHO website, it actually is the WHO’s website embedded in the malicious page, with a simple pop up box over top (see below).
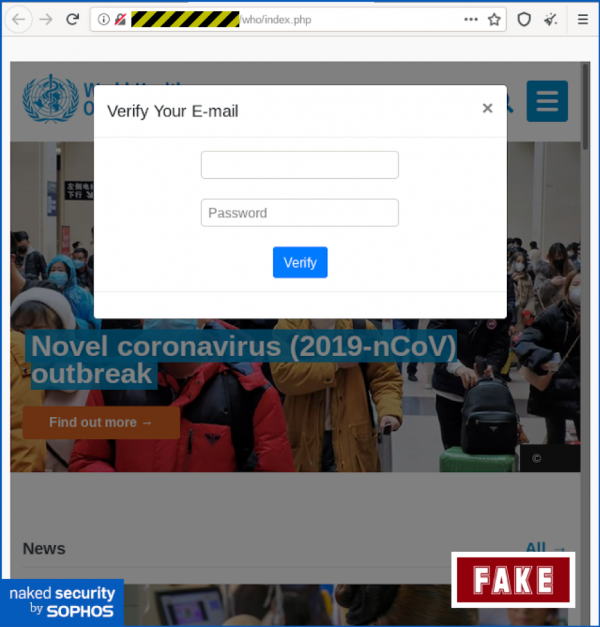
WHO phishing site. Source: Sophos and Whalebone
Here’s another slick and easy to believe example of a phishing email purporting to be an airbnb update.
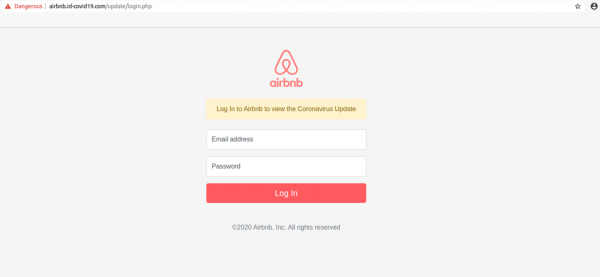
Airbnb phishing site. Source: Whalebone
How to stay safe
The global scope of the threats, both in the real world and online, illustrate the seriousness of the problem. It’s now more than ever essential to keep your valued users safe and secure. To do so, Whalebone has created a product uniquely suited to provide telco operators and their customers with the security they need. Unobtrusive, providing only a users’ consent at the point of sale or via a call line, residing on the network at the DNS level, offering rapid return on investment and the fastest possible time to market, whalebone is ready and waiting to help you protect your customers in these trying and dangerous times. For more information, visit the Whalebone webpages here or contact a Whalebone consultant today.



